Overview Table: Mobile Virus Risks and Protection at a Glance
| Risk Area | How Viruses Enter | Common Warning Signs | Core Prevention Method |
|---|---|---|---|
| Malicious apps | Unofficial app stores, fake apps | Battery drain, ads | Install apps carefully |
| Phishing attacks | Fake messages and links | Account compromise | Link awareness |
| Unsafe networks | Public Wi-Fi misuse | Data leaks | Secure connections |
| Outdated software | Missing security patches | System instability | Regular updates |
| Excess permissions | Over-privileged apps | Privacy breaches | Permission control |
| Infected files | Downloads, attachments | Performance drop | File scanning |
| Weak settings | Default security options | Easy exploitation | System hardening |
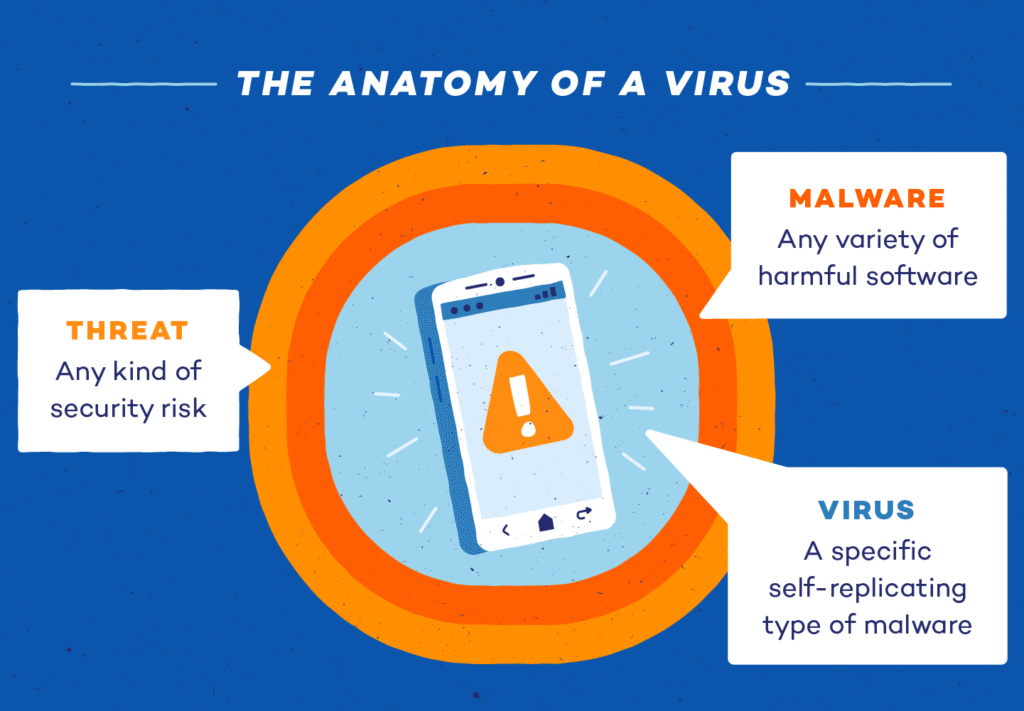
Understanding What Phone Viruses Really Are
The idea of a Phone Safe from Viruse often feels abstract. Phones are seen as personal, closed devices, very different from traditional computers. In reality, smartphones are powerful computing systems that store sensitive data, connect continuously to the internet, and run thousands of lines of code through apps and services. This makes them attractive targets for malicious software.
A Phone Safe from Viruse is not always a dramatic system failure. Most mobile threats are designed to be subtle. Their goal is often to steal data, track behavior, show intrusive ads, or quietly exploit system resources. Unlike classic computer viruses that spread aggressively, mobile malware focuses on persistence and invisibility.
Understanding how these threats work is essential to preventing them.

Smartphones have become the center of modern life. They store personal conversations, financial information, work documents, photos, and access to countless online services. As phones have grown more powerful and connected, they have also become attractive targets for malicious software. The idea that mobile devices are naturally safe is no longer accurate in today’s digital environment.
Phone Safe from Viruse and mobile malware rarely announce themselves openly. Instead of causing obvious system crashes, they often work quietly in the background, collecting data, displaying intrusive ads, or exploiting system resources. Many users only notice a problem when performance drops, battery life worsens, or accounts are compromised. By then, damage may already be done.
How Mobile Viruses Enter Your Phone
Malicious Applications and Fake Apps
Apps are the primary entry point for mobile malware. Fake versions of popular apps, modified games, and utility tools often hide malicious code inside otherwise functional software.
Once installed, these apps may request excessive permissions that allow them to monitor activity, display ads, or access sensitive data.
Phishing Messages and Social Engineering
Phone Safe from Viruse do not always enter through apps. Many attacks begin with a message that convinces users to click a link or download a file.
These messages may appear as delivery notifications, bank alerts, or account warnings. The goal is to trick users into installing malicious software or revealing credentials.
Unsafe Downloads and Attachments
Downloading files from untrusted websites or opening unknown email attachments exposes Phone Safe from Viruse to risk. Even documents and images can be used to exploit vulnerabilities if the system is outdated.
Public Wi-Fi and Network Exploits
Unsecured public Wi-Fi networks allow attackers to intercept data or redirect users to malicious websites. While Wi-Fi itself does not install Phone Safe from Viruses, it enables attacks that can lead to infection.
Differences Between Android and iPhone Security
Android’s Open Ecosystem
Android allows greater flexibility in app installation and system customization. While this benefits advanced users, it also increases exposure to malicious apps, especially when apps are installed outside the official store.
Android malware often focuses on ad fraud, data theft, and subscription scams.
iPhone’s Controlled Environment
iPhones use a tightly controlled app ecosystem, making large-scale malware outbreaks less common. However, this does not make iPhones immune.
Phishing, configuration profile abuse, and account-based attacks remain significant risks.
Common Ground Between Platforms
Regardless of platform, user behavior remains the weakest link. Unsafe links, reused passwords, and ignored updates affect both systems equally.
Early Warning Signs of a Virus on Your Phone
Unusual Battery Drain
Malicious apps often run background processes continuously. This leads to noticeable battery drain even during light usage.
Overheating and Performance Drops
Phone Safe from Viruse infected with malware may overheat or slow down due to hidden activity. Lag during simple tasks is a warning sign.
Unexpected Ads and Pop-Ups
Frequent ads outside of apps or sudden redirects indicate adware infection.
Unknown Apps or Settings Changes
Apps you do not remember installing or settings changed without permission should raise concern.
Increased Data Usage
Malware may transmit data silently. A sudden spike in data usage is often overlooked but highly suspicious.
Core Principles of Mobile Virus Protection
Prevention Over Removal
Preventing infection is far easier than removing malware. Most damage occurs before users realize a threat exists.
Strong habits reduce risk significantly.
Minimalism in App Installation
Every app increases attack surface. Installing fewer, well-reviewed apps reduces exposure.
Awareness and Skepticism
Most mobile threats rely on user trust. Questioning messages, links, and downloads blocks attacks at the earliest stage.
Securing Your Phone at the System Level
Keeping the Operating System Updated
System updates include security patches that fix known vulnerabilities. Delaying updates leaves doors open for attackers.
Regular updates are the foundation of mobile security.
Enabling Built-In Security Features
Both major mobile platforms include security tools such as app scanning, sandboxing, and permission monitoring.
Ensuring these features are active strengthens baseline protection.
Using Strong Lock Screen Protection
A strong PIN, password, or biometric lock prevents unauthorized access if the Phone Safe from Viruse is lost or stolen.
Physical access often leads to digital compromise.
Safe App Installation Practices
Downloading Apps from Trusted Sources
Official app stores apply security checks that reduce malware risk. While not perfect, they provide a critical Phone Safe from Viruse layer.
Avoid installing apps from links or unknown websites.
Reading Permissions Carefully
Permissions reveal an app’s true intent. A calculator app requesting access to contacts or messages is suspicious.
Deny unnecessary permissions proactively.
Monitoring App Behavior After Installation
Even trusted apps can change behavior after updates. Unusual activity should prompt review or removal.
Protecting Against Phishing and Online Scams
Recognizing Fake Messages
Urgent language, spelling errors, and suspicious links are common phishing indicators.
Legitimate organizations rarely demand immediate action via messages.
Avoiding Direct Link Clicks
Instead of clicking links, access services through official apps or websites manually.
This habit neutralizes most phishing attempts.
Securing Accounts with Strong Passwords
Weak or reused passwords magnify damage when phishing succeeds.
Unique passwords limit breach impact.
Managing Network and Connectivity Risks
Using Public Wi-Fi Cautiously
Avoid accessing sensitive accounts on public networks. If necessary, limit activity to basic browsing.
Disabling Auto-Connect Features
Auto-connecting to open networks increases exposure. Manual connection provides control.
Monitoring Bluetooth and Nearby Sharing
Leaving Bluetooth active unnecessarily exposes the device to proximity-based attacks.
Disable unused connectivity features.
Role of Mobile Security Applications
When Antivirus Apps Help
Security apps can detect known threats, block malicious links, and warn about risky behavior.
They are most useful for users who install many apps or browse frequently.
Limitations of Antivirus Solutions
No app can protect against all threats. Security tools supplement, not replace, Phone Safe from Viruse habits.
Overreliance creates a false sense of security.
Data Protection and Backup Strategies
Regular Backups as a Safety Net
Backups ensure data recovery if malware forces a device reset.
They also reduce fear-driven decisions during incidents.
Encrypting Sensitive Data
Encryption protects personal information even if malware gains partial access.
System-level encryption should remain enabled.
What to Do If You Suspect a Virus
Immediate Steps
Disconnect from the internet to stop data transmission. Identify suspicious apps and remove them.
Restarting the Phone Safe from Viruse may temporarily stop malicious processes.
Safe Mode and App Removal
Phone Safe from Viruse mode disables third-party apps, allowing identification of the source.
Removing recently installed apps often resolves the issue.
Factory Reset as a Last Resort
If malware persists, a factory reset eliminates most infections. Restoring from a clean backup prevents reinfection.
Long-Term Habits for Mobile Security
Regular Security Reviews
Periodically reviewing installed apps, permissions, and settings keeps threats in check.
Consistency matters more than intensity.
Staying Informed About Threat Trends
Understanding common scam patterns improves detection.
Awareness evolves alongside threats.
Teaching Security Awareness to Others
Shared devices and family accounts introduce indirect risk.
Educating others protects the entire digital ecosystem.
Common Myths About Phone Viruses
“Phones Cannot Get Viruses”
This belief leads to careless behavior. Phone Safe from Viruse are vulnerable in different but real ways.
“Only Android Gets Malware”
Both platforms face threats, though methods differ.
Security is behavioral, not brand-based.
“Antivirus Alone Is Enough”
No single tool replaces cautious usage.
Defense requires layers.
Final Thoughts: Security as a Daily Practice
Keeping your phone safe from viruses is not about fear or technical expertise. It is about awareness, discipline, and consistency. Most mobile infections succeed not because systems are weak, but because habits are predictable.
A secure Phone Safe from Viruse is the result of small, repeated actions: updating regularly, questioning links, installing apps thoughtfully, and monitoring behavior. These actions require minimal effort but deliver long-term protection.
In an age where Phone Safe from Viruse store personal, financial, and professional lives in one place, mobile security is no longer optional. Treating phone Phone Safe from Viruse as a daily practice rather than a one-time setup ensures that your device remains a tool of convenience, not a point of vulnerability.

